Rules
The Rules module is used to create, query, and manage risk rules.
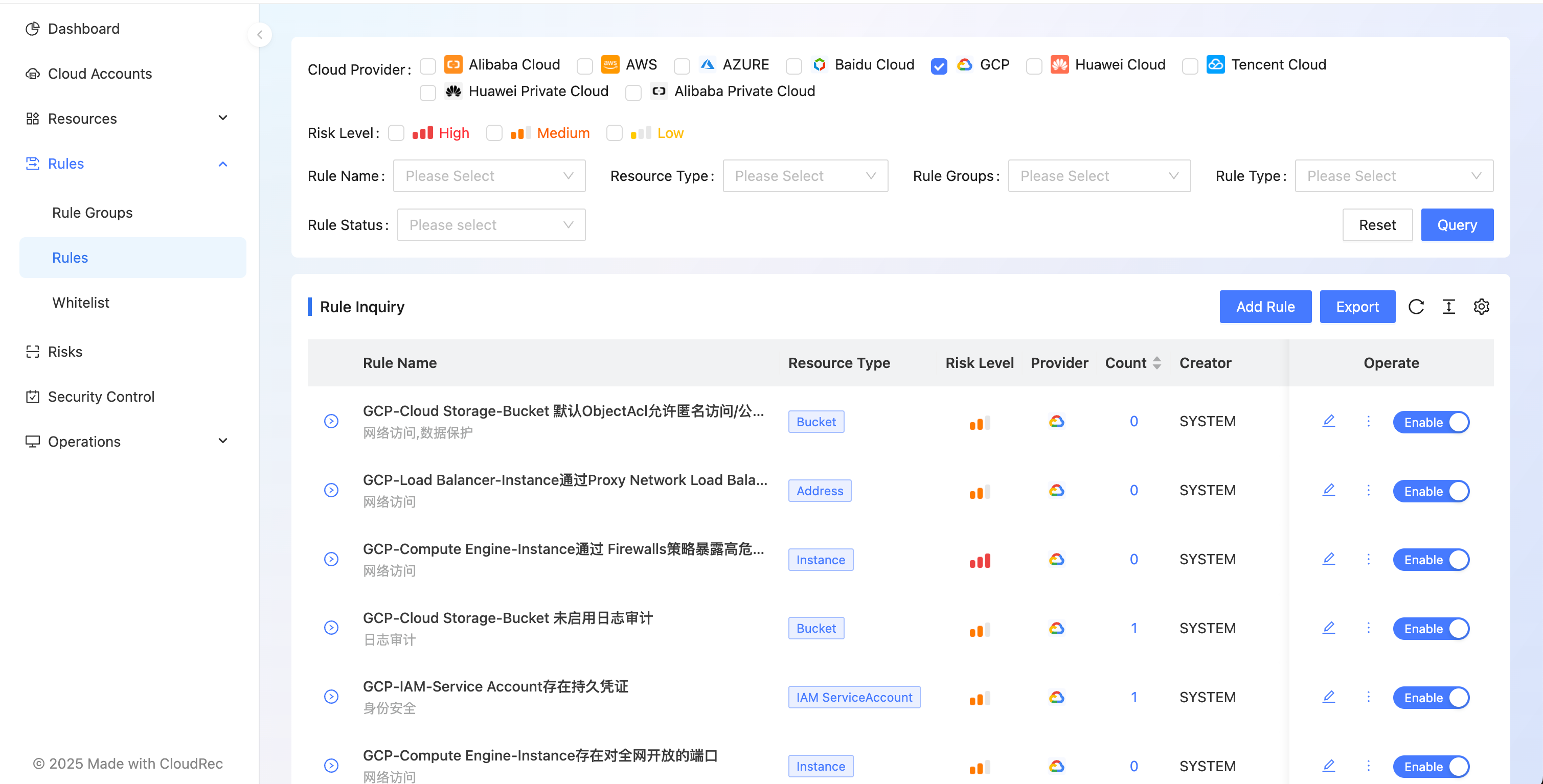
How to create rules
- click the [Add Rule] button on the right
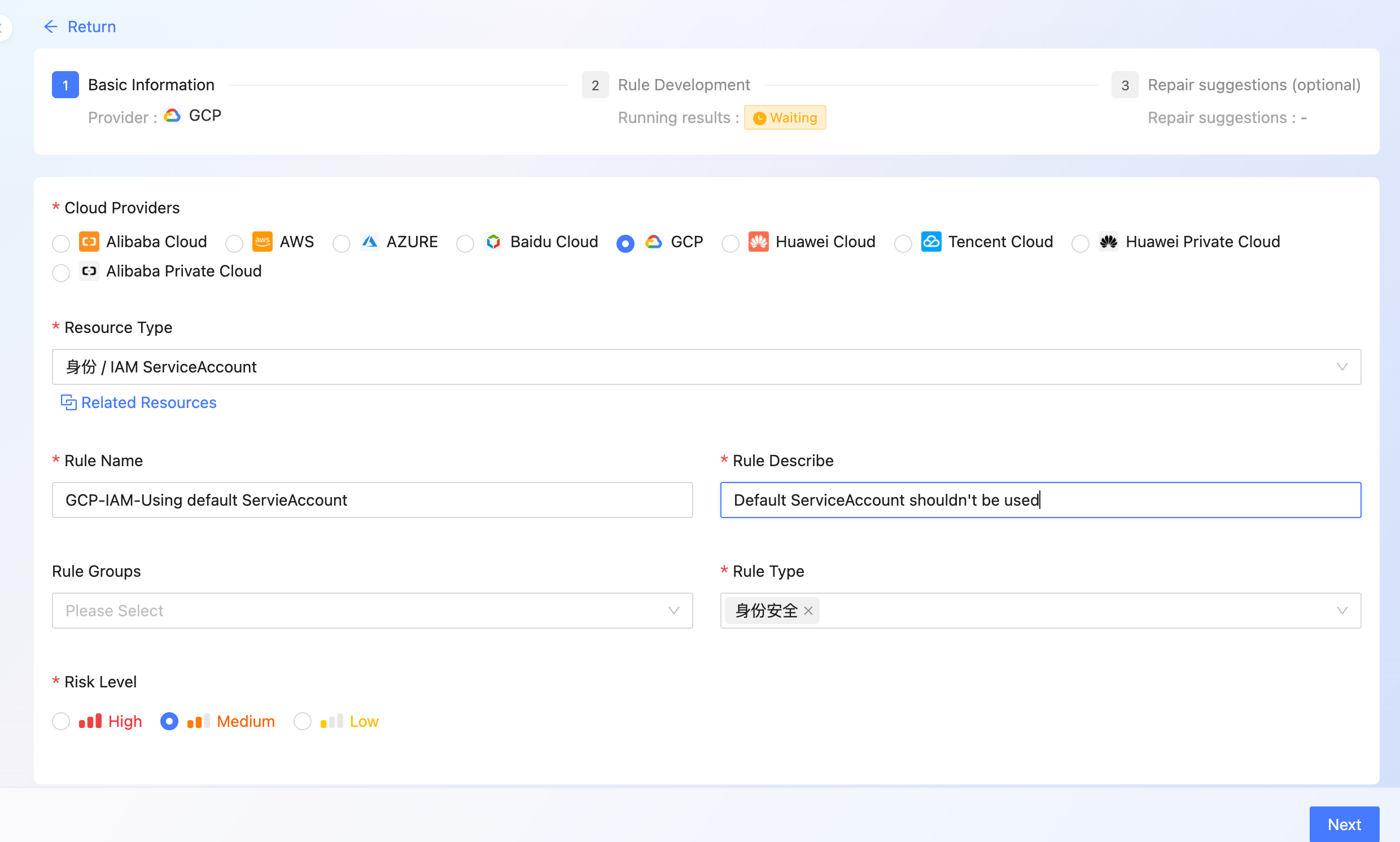
- select [Cloud Providers]
- select [Resource Type]
- input [rule name] and [rule description]]
- select [Rule Group], [Rule Type] and [Risk Level]]
- click [Next] to enter the rule development page
- the [INPUT] section in the upper-right corner of the page body indicates that the system selects an instance configuration from existing resources for rule debugging. The resource type is the same as that selected in the previous step.
- [The Rego PlayGround] on The left side of The main body is The place where Rego rules are developed and edited.
- Click [Execute] in the upper right corner and run rego. The result is displayed in [OUTPUT] in the lower right corner]
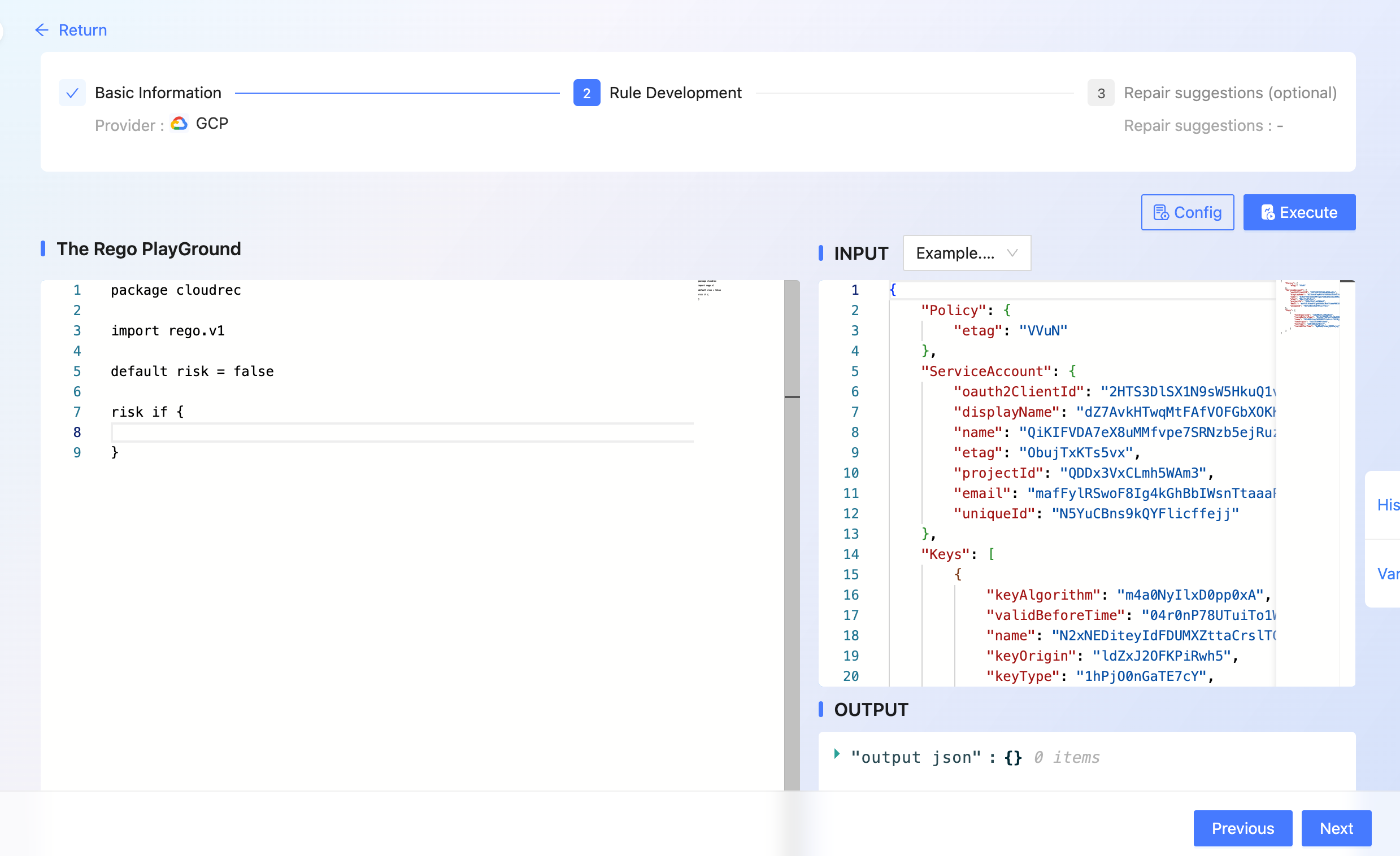
- after completing the rule development and dryrun, click [Next] to enter the repair suggestion page
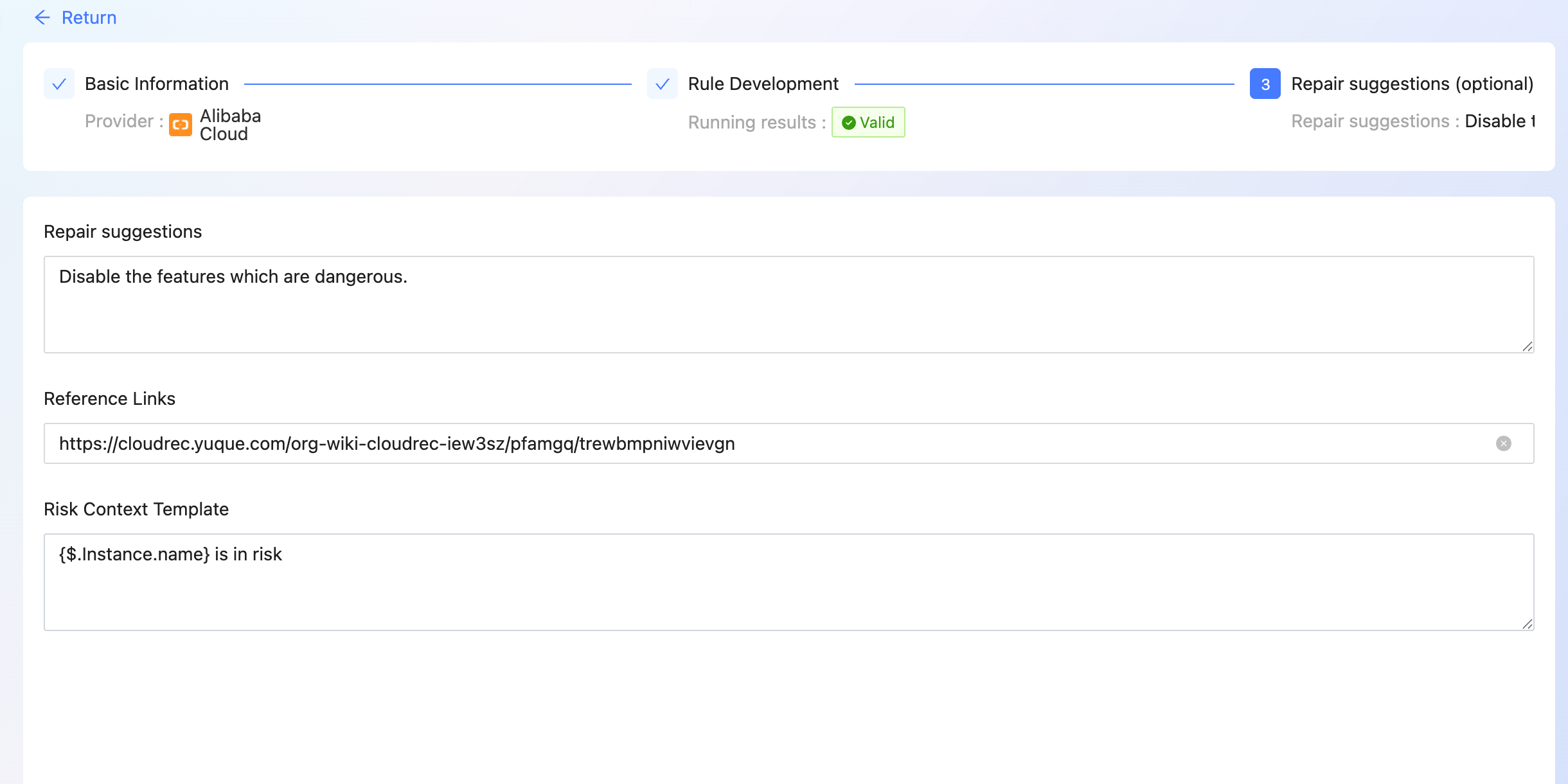
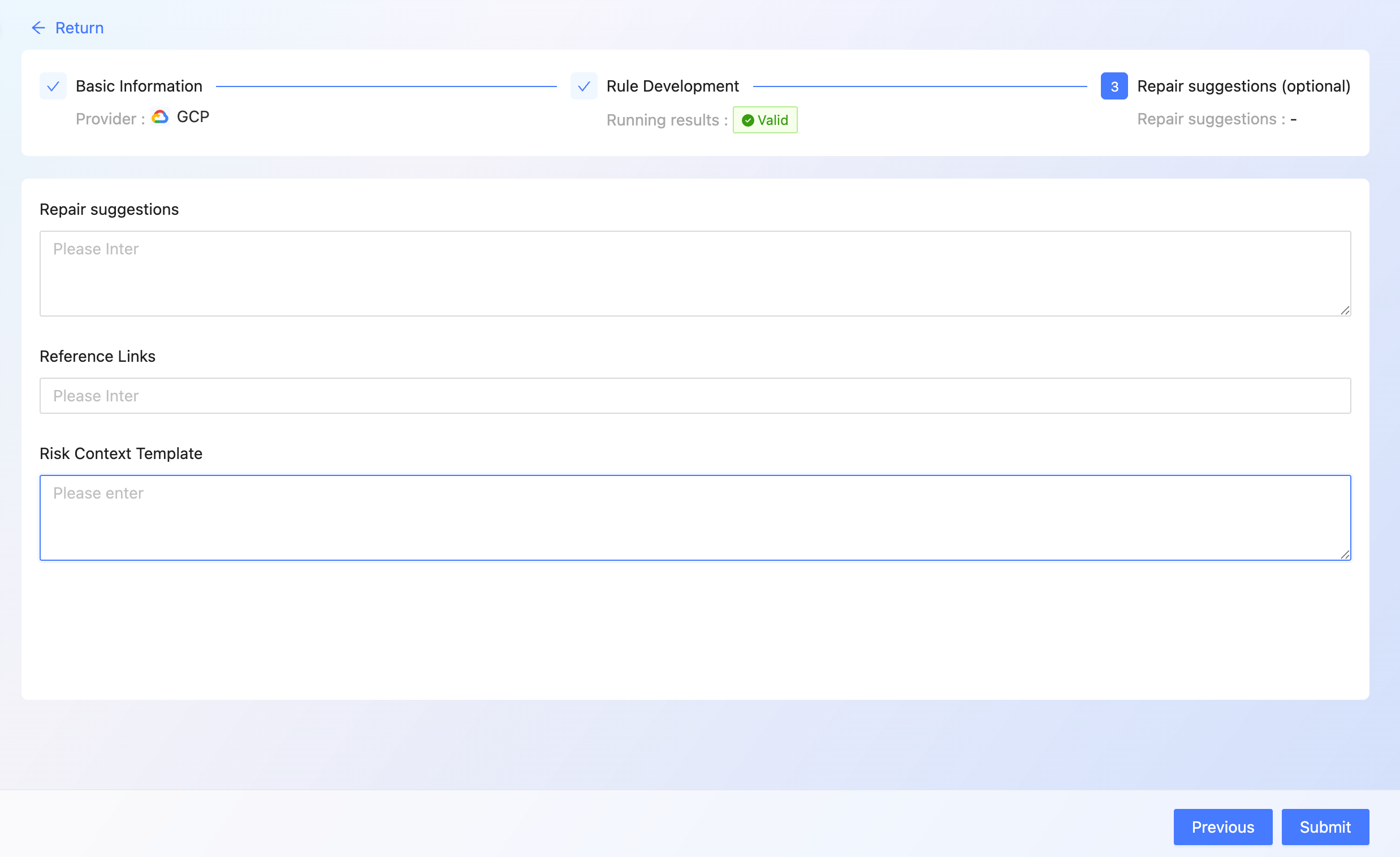
- complete [Repair Suggestion], [Reference Links], [risk Context Template ]
- click [Submit]
function
associate two different resources to address scenarios where data access across resource types is required for risk analysis.
We collect configurations such as security groups and ACL as a separate resource (Resorce). If you need to perform ECS Security Group configuration detection and LB ACL configuration detection, you need to associate the two resources on the platform.
Process
for example, when analyzing the risk that an Alibaba Cloud ECS instance is open to the entire network, you need to associate [ECS instance] with [security group] resources.
- Select Alibaba Cloud as the cloud platform and Compute/ECS as the resource type]
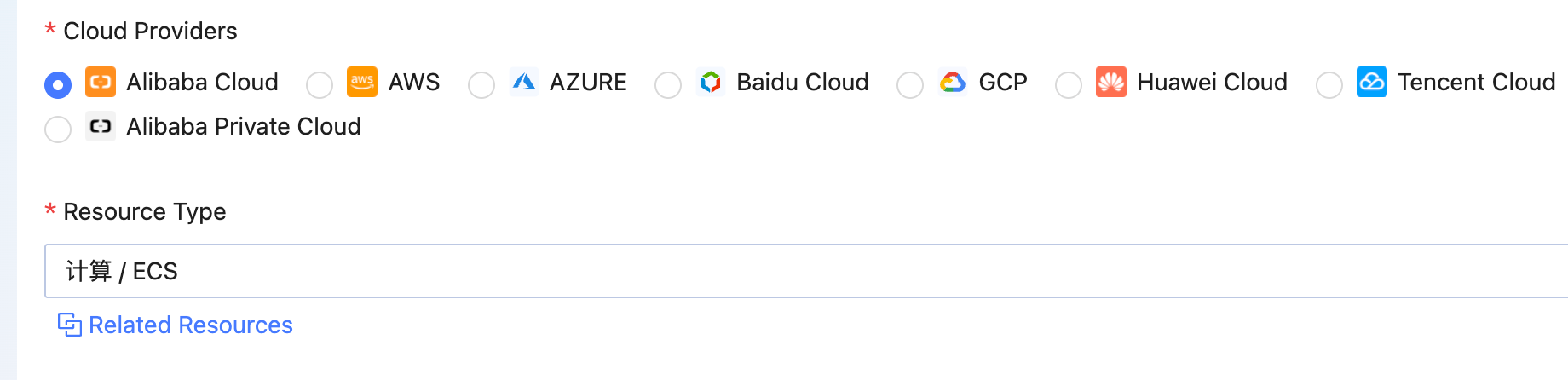
- at this time, you need to associate the resource data of the security group, and click [Related Resources] to configure it.
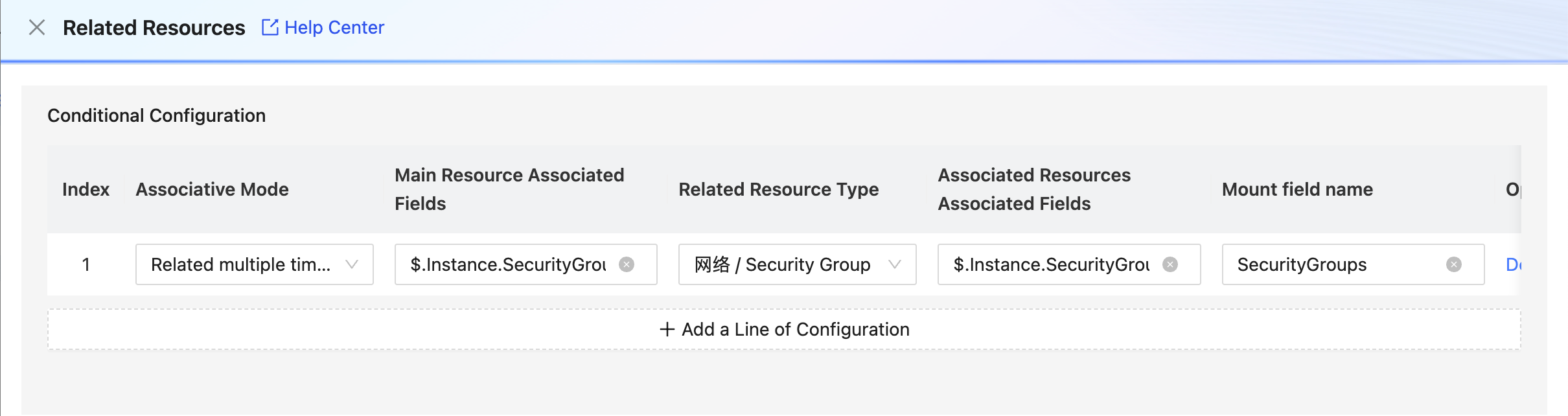
- resource Type: Select the resource type to be associated.
- Main resource Key: the ECS resource is used for the associated field, for example:
- associated resource Key: the field used to associate security group resources, such:
- mount field name: the data associated to will be mounted on the new field
- results after correlation
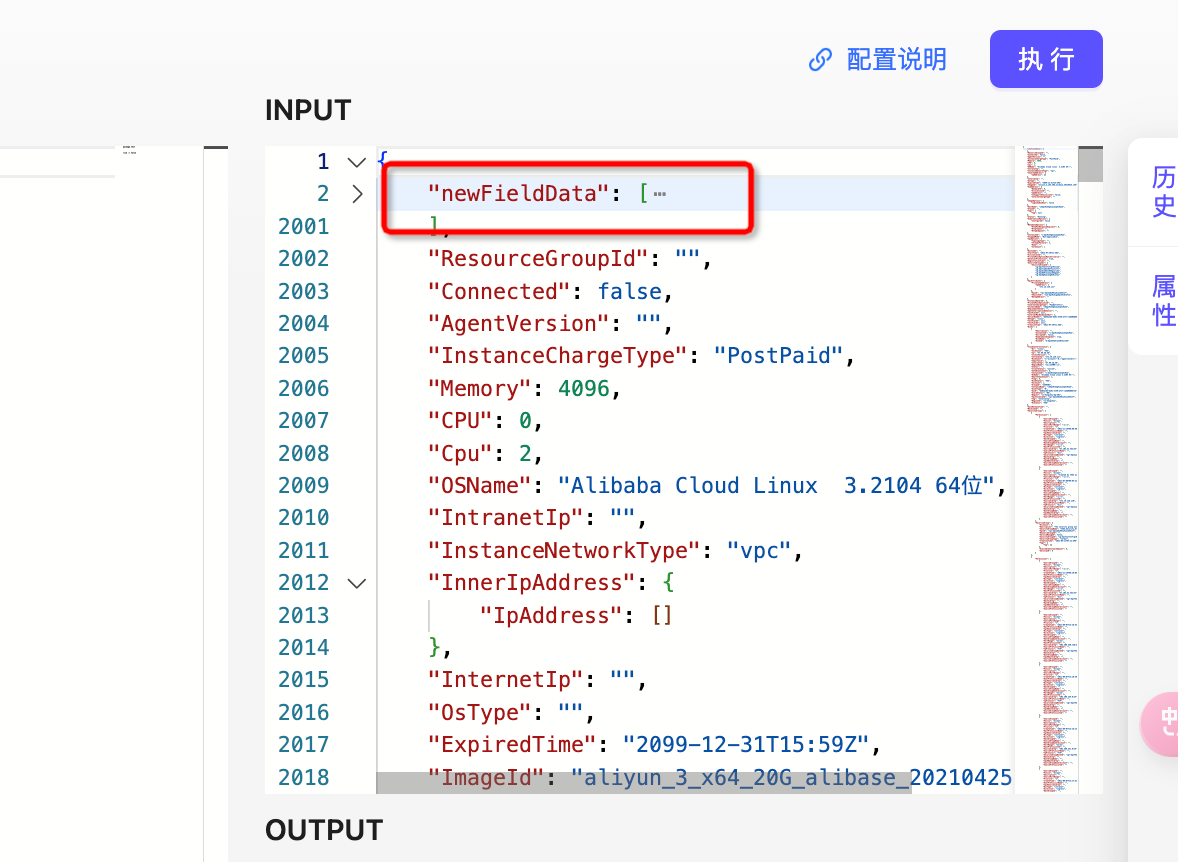
description
value method
path Rule Description
{
"store": {
"book": [
{
"category": "reference",
"author": "Nigel Rees",
"title": "Sayings of the Century",
"price": 8.95
},
{
"category": "fiction",
"author": "Evelyn Waugh",
"title": "Sword of Honour",
"price": 12.99
},
{
"category": "fiction",
"author": "Herman Melville",
"title": "Moby Dick",
"isbn": "0-553-21311-3",
"price": 8.99
},
{
"category": "fiction",
"author": "J. R. R. Tolkien",
"title": "The Lord of the Rings",
"isbn": "0-395-19395-8",
"price": 22.99
}
],
"bicycle": {
"color": "red",
"price": 19.95
}
},
"expensive": 10
}$.store.bicycle.color | ||
<font style="color:rgb(31, 35, 40);">$.store.book[*].author </font> |
reference documentation: https://github.com/json-path/JsonPath
association Method
the main resource Key and the associated resource Key are evaluated by using the json path expression. When the two values are equal, they are associated. One-to-one and one-to-many associations are supported.
- One-to-one association example:
sample data A:
{
"field1":"i-xxxxxxxxxx",
"field2":"xxx"
}sample data B:
{
"field3":"i-xxxxxxxxxx",
"field4":"xxx"
}configure $.field1 and $.field3, and mount the field name newField to generate the result.
{
"field1":"i-xxxxxxxxxx",
"field2":"xxx",
"newField":{
"field3":"i-xxxxxxxxxx",
"field4":"xxx"
}
}- One-to-many association example
sample data A:
{
"field1":["i-xxxxxxxxxx"],
"field2":"xxx"
}sample data B:
{
"field3":"i-xxxxxxxxxx",
"field4":"xxx"
}configure $.field1 and $.field3, and mount the field name newField to generate the result.
{
"field1":"i-xxxxxxxxxx",
"field2":"xxx",
"newField":[
{
"field3":"i-xxxxxxxxxx",
"field4":"xxx"
}
]
}Risk Context Template
the risk context template is used when subscribing to alarms to facilitate subscribers to quickly understand risk details. How to use the configuration to subscribe to alarms Read subscribe to Alerts .
Example of results
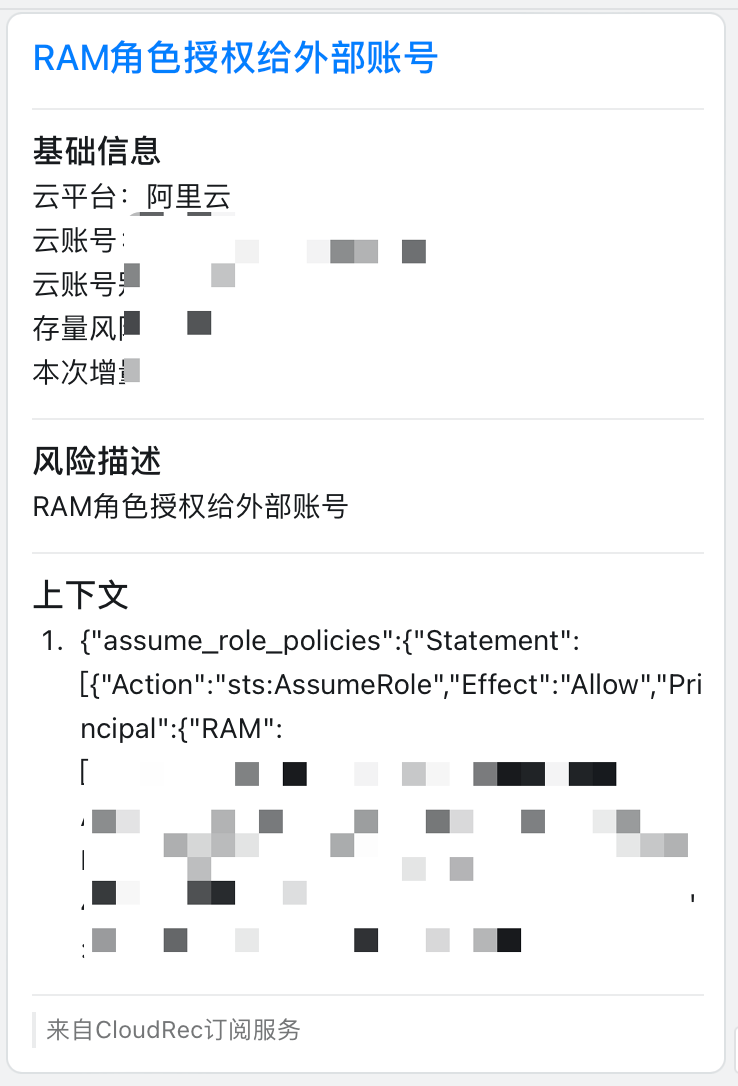
how to configure risk context templates
- when not configured, the full output of the Rego rule is used as the context by default.
- Use the jsonPath output from the run of the Rego rule to take the value from. The configuration method is as follows:
{$.Instance.name} is in risk